Border Check, the physical and political realities behind the internet
Posted in: Uncategorized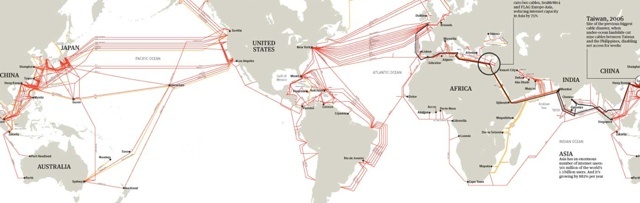

The Pod, designé par Formwerkz Architectz, est le tout nouvel hôtel capsule de Singapour. Les cabines empilées les unes sur les autres, caractéristique première des hôtels capsules, sont plus spacieuses et offre un peu plus d’intimité. Un très bel hôtel, magnifiquement réalisé, à découvrir en images.

Some things are still scared, but your privacy on corporate-owned communications networks is not, and never has been.

This fact of digital life has been evident for years, but the recent revelation that the National Security Agency is working closely with leading tech companies, makes it crystal clear–anything you write, say, record, transfer etc. is subject to inspection by a federal employee tasked with keeping America secure from terror attacks.
Tech companies could stand tall and say yes, we help keep America safe from terror. But they’ve chosen to deny their involvement instead.
This is what The Google has to say for itself:
We have not joined any program that would give the U.S. government—or any other government—direct access to our servers. Indeed, the U.S. government does not have direct access or a “back door” to the information stored in our data centers. We had not heard of a program called PRISM until yesterday.
Thankfully, Foreign Policy breaks down the geek’s coded language for us.
According to Chris Soghoian, a tech expert and privacy researcher at the American Civil Liberties Union, the phrase “direct access” connotes a very specific form of access in the IT-world: unrestricted, unfettered access to information stored on Google servers. In order to run a system such as PRISM, Soghoian explains, such access would not be required, and Google’s denial that it provided “direct access” does not necessarily imply that the company is denying having participated in the program.
A similar logic applies to Google’s denial that it set up a “back door.” According to Soghoian, the phrase “back door” is a term of art that describes a way to access a system that is neither known by the system’s owner nor documented. By denying that it set up a back door, Google is not denying that it worked with the NSA to set up a system through which the agency could access the company’s data.
Yes, the company that vows to “do no evil,” not only engages in domestic spying on its users, it uses doublespeak to cloak its activities and protect its brand value.
As users or consumers of these networks, we have few places to turn. The connected networks we know as the Internet is a classic monopoly, conceived by the military and managed by their corporate contractors. Yet, we think of it as the peoples’ media. Why? Are too bedazzled by the promise of riches to pay attention to the facts? Or just lost in another cute cat video?
For me personally, I return time and again to the importance of media literacy. If we are not able or willing to turn away from the machine, we need to know how to live with it and work with it. And this means knowing what it is, how it works, who owns which piece and so on. Media literacy is also of the essence when flithy-rich corporate entities, and the government, use language to intentionally mislead people.
The post Google’s PRISM-Driven Doublespeak Needlessly Misleading appeared first on AdPulp.


Would you stand up for a friend? No, seriously, if a friend called in the middle of the night and needed you to bail them out of a poker game gone wrong, would you rush over there with the ransom money to free your homey?
Carlsberg drinkers would.
Will Burns, CEO of Ideasicle loves the idea.
Carlsberg shattered the cliches while positioning itself as a brand for close (very close) friends. Here’s why I love this reality-prank idea: Carlsberg isn’t flatly claiming their beer is for those times when friends are together. They are demonstrating it.
David Gianatasio of Adweek notes:
The poker prank, while elaborate and invasive, actually seems a tad tame by the genre’s current standards. It’s nowhere near as shocking as last week’s faux elevator strangling for the movie thriller Dead Man Down, or as intricately upsetting as Nivea’s airport ambush in February, which strove to convince people that they were wanted by the law.
Duval Guillaume Modem/Antwerp is the responsible party, or irresponsible party depending on your POV.
Legendary copywriter and author Luke Sullivan, who now teaches advertising at SCAD in Savannah, weighed in on another new “shock and awe’ stunt from Pepsi MAX this morning:
I HATE THESE AD “PRANKS” THAT SCARE THE HELL OUT OF PEOPLE. SHAME ON THE BRANDS AND SHAME ON THE AGENCIES. What agency did this? I’d love to post a note on their site.
Here’s the footage he’s speaking of (btw, the Pepsi MAX looks to be from TBWA\Chiat\Day):
What are you thoughts on this invasive species?
The post No One Was Hurt During The Making Of This Invasive Advertising appeared first on AdPulp.


