Can’t believe how late i am in publishing these notes about the Transmediale exhibition. I used to be a young, dynamic and super fast blogger, but that was a long time ago.

Although i always chose to focus on the good side of exhibitions and other events, i rarely have the opportunity to be so genuinely and totally enthusiastic about a festival. This was the media art festival i was dreaming of: a strong concept, an exhibition that does not confuse new media art with circus of interactivity and electro-gadgets for grown-ups, a conference that calls in so many inspiring artists, activists and researchers.
The theme? Conspire. How could you resist that one? While doing some research on conspiracy theories i passed from the expected to the utterly ridiculous (with a few nuggets in the middle). Conspiracy theories spread faster than ever with a little help of the internet and other communication technologies, but more importantly there is no doubt that we are definitely living an era where suspicion (or should i say paranoia?) reigns supreme.

Matt O’Dell, New Worship, image courtesy galerie Schleicher+Lange, Paris
“Conspiracy is the ‘condition’ of our times,” told me Stephen Kovats, the Director of the festival. “When we consider information and network culture, when we look at the questions arising from the relationships between politics and culture particularly online … the loss of authorship – or perhaps authority or belief in universal truths … the weaving of narrative together with speculation and expanding the results at light speed, where anybody anyplace can become an expert or authority on any issue … that’s where the stuff of conspiracy is born. With transmediale, we were interested in exploring what this ‘condition’ in the era of digital mobility as a strategy, emotion, aesthetic, cultural state of being or landscape is.
Learning to harness the mechanisms of conspiracy, or those of the conspiratorial act also empower us as creative individuals to better understand the irrational culture of fear and security being imposed on us.”
One of the best moment of the festival for me was PN (Power Noise), a electrifying performance by Elpueblodechina and Zosen who turned the data grabbed from Bureau d’Etudes‘ Bohemian Map into noise.

Video
The Bohemian Map maps the connections and sphere of influence of some 2000 members of the Bohemian Grove, the high-profile annual Sonoma retreat of the Bohemian Club, a group that counts some of the most powerful men in the world. The club has counted every Republican president since Herbert Hoover as a member. Based in Paris, the Bureau d’Etudes group is engaged in the mapping of contemporary power relations at the institutional and international level.

Breakfast at Owls Nest Camp, Bohemian Grove, July 23, 1967 (image)
Bureau d’Etudes (whose work i’ve been admiring for years even if i’ve never written about them so far, shame on me!) was participating to the Transmediale exhibition with one of their latest projects, the Laboratory Planet. While so far they were producing gorgeous large-scale posters that visualize structures of power and ownership which usually remains invisible, this project uses google maps to reveal the laboratory for experimentation that our planet has become. After the end of WW2, the Earth, along with all its living inhabitants, have become a huge site for all kinds of experimentations.
The development of convergent technologies (bio-, nano-, cogno-, info-, robo-, sociotech) is the magic circle in which biological and mechanical species emerge
from the laboratory and from new periodic tables. Much of this research is today carried
out in secret. That is why an understanding of the present itself remains determined by the limited insight that we can have concerning information which is itself filtered or orchestrated. How can we speak of the present ? How can we know where we are or understand the situation we find ourselves in ?
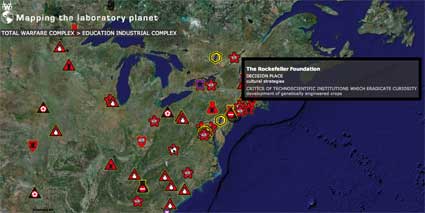
Laboratory Planet aims to be a data base which would give us both a broad vision of the phenomenon, but also a local one as you can check the map and see what is happening in your neighbourhood. It’s also an instrument that calls for the collaboration of the public to enrich its content.
More details in the PDF of the project.
The exhibition, guest-curated by NataÅ¡a PetreÅ¡in-Bachelez, requests some effort from the visitor. Nothing is right here right now, nothing comes to you easily, and even if you visit it equipped with the leaflet that describes each work, there are still a number of questions that you’ll have to investigate by yourself if you want an answer. This way of experiencing the projects fits perfectly the mysterious streak of the exhibition theme.
The show is organized around several “thematic constructs”, each of them explores a different facet of notions such as conspiratorial truths, bio-organic systems and twisted realities.
Back to the theories of conspiracy with Christoph Keller‘s project Chemtrails.

The Chemtrail conspiracy theory claims that some trails left behind jet aircraft are different in appearance and quality from those of normal contrails, may be composed of harmful chemicals, and are being deliberately produced, and covered up by the government. These unusual trails are referred to as “chemtrails”. Some researchers believe that a chemical and/ or biological agent of some sort is being released. The term “chemtrail” does not refer to common forms of aerial dumping – it specifically refers to systematic, high-altitude dumping of unknown substances for undisclosed purposes, resulting in the appearance of these unusual contrails.

Photo: Jonathan Gröger
Keller’s work includes a video and a collection of photos taken by amateurs. Chemtrails uses the mysterious phenomenon to reflect on superstition and paranoia in the USA.

Wonder Beirut #1, Greetings from Beirut, 1998-2007
The first part of Wonder Beirut, by Joana Hadjithomas and Khalil Joreige, tells the story of a pyromaniac Lebanese photographer named Abdallah Farah.

Wonder Beirut #21, Beaches in Beirut, 1998-2007
In 1968 and 1969 Farah took photos of the capital for the Beirut tourist authority intended to promote the city. The resulting postcards depicted an idealized Lebanon in the 1960s. The postcards are still on sale nowadays , although most of the places they represent were destroyed during the Lebanese civil war.

Latent Images, 1998-2007
In the autumn of 1975, Farah started damaging the negatives of his postcards, burning them according to the destruction of the buildings he saw disappearing because of bombings and street battles.
The “Wonder Beirut” project shows the results of Farahs photographical and pyromaniacal work. Part of the project are also the notes of Farah documenting the photographs which he never developed because of the lack of fixative and photographic paper during the war years. By publishing and distributing these images, the artists try to fight the trend which puts the Lebanese civil war between brackets and includes the Lebanese conflict only marginally in the contemporary history. But is this postcard story a fact or a fiction? (more images.)
The story of Be Prepared! Tiger!, a project by Knowbotic Research in collaboration with Peter Sandbichler, starts with the discovery on the internet of a propaganda video by the Tamil liberation army which shows the glorification of a speedboat that was supposedly financed by North Korea. The boat is deliberately likened to the American F 117 stealth bomber, a myth of invisibility and invincibility. The artists gathered information inside different networks and through private contacts in order to re-engineer and rebuild the boat.
The boat is mysterious in its background, form and tests have shown that it remains invisible for radar systems. Yet, the boat can be seen with the naked eye, it is functional, and it is even a marketable good (the artists put it for sale on various websites.)

With their project, the artists play on the dialectics of visibility and invisibility present in many of our modern technologies, it stands for the ruses and tactics used to escape from the geo positioning and surveillance technologies of the 21st century.
Also part of the Transmediale exhibition: Chernobyl Project – Images of the Invisible, Amazon Noir – The Big Book Crime, Symbology.
To amuse the crowd on their way to the restaurant, the absorbing Standard Time by Datenstrudel. A 24h clock/video showing 70 workers building somewhere in Berlin and “in real time” a wooden 4 x 12 m “digital” time display: a work that involves 1611 changes within 24 hour period.

Photo Jonathan Gröger
The spectator looking at Standard Time does not only see the time, but also people tirelessly constructing it. Video.

And on the way from the restaurant to the bar…
5VOLTCORE‘s knife.hand.chop.bot uses a knife to s(t)imulate the test of courage – a kind of game known as “Five Finger Fillet”. The User puts his/her hand into the Machine and pushes the button. The knife starts to hit the space between the fingers, first slowly then continually getting faster. A sensor guides the Machine so it “knows” where to hit.

Electric contacts are activated as soon as the first “nervous sweat” is detected on the hand, the sweat turns the skin into a conductor. Disturbed by the electric current that is now transmitted via the skin, the computer changes behaviour: sounds are generated by the closure of the contacts (circuit bending) that can either be interpreted as warning or act as an additional source of stress. On the other hand, they can have an effect on the position of the knife which is controlled by the computer and thereby hurt the potential perpetrator of the disturbance.
All my images are online.








![Exhibition tip - GaMe! at the [DAM] gallery in Berlin 47k](http://www.we-make-money-not-art.com/wow/0acahsseorganj0-640.jpg)